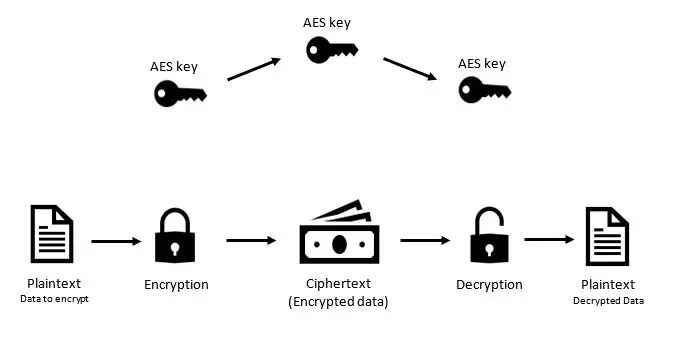
Solid-state drives (SSDs) and their affiliated technology continue to evolve rapidly. In recent years, SSDs have made major strides in lowering latency, boosting efficiency, and enhancing performance—and it’s clear that the future will bring further time- and labor-saving refinements. It’s also true, however, that all these innovations to SSD technology have left end users with […]
SSD Interfaces: SAS vs. SATA vs. NVMe