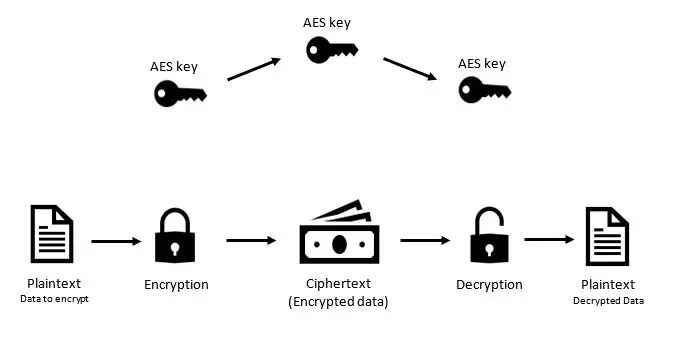
One of the most secure ways to protect data is to use encryption systems. However, there are no standards to govern data encryption systems and the algorithms they use to turn plain text into encrypted data. That’s why organizations in the private sector simply choose the data encryption system that works best for them. However, […]
What Is FIPS 140-2 Level 3?